Ethical Hacking is a discipline widely followed by major big-wigs of the tech industry to protect their organization against any forthcoming probes from black hat hackers. In this Ethical Hacking Tutorial, I’ll be discussing some key points of this discipline that is being followed around the globe. The following topics will be discussed:
- What is Ethical Hacking?
- Ethical Hacker Roles
- Why is Ethical Hacking Important?
- What is a Security Threat?
- Types of Security Threats
- Security Threats: Preventive Measures
- Ethical Hacker Skills
- Why Learn Programming?
- Ethical Hacking Tools
- What is Social Engineering?
- Social Engineering Techniques
- Cryptography
- Standard Cryptographic Algorithms
- RC4 Decryption Demonstration
Ethical Hacking Tutorial For Beginners | Ethical Hacking Course | Ethical Hacking Training | Edureka
This Edureka “Ethical Hacking Tutorial for Beginners” video will give you an introduction to Ethical Hacking. This video will talk about key topics of Ethical Hacking for beginners!
What is Ethical Hacking?
The act of hacking is defined as the process of finding a set of vulnerabilities in a target system and systematically exploiting them. Ethical Hacking as a discipline discerns itself from hacking by adding a vital element to the process – ‘consent’. The addition of ‘consent’ to this process serves two objectives –
- The process becomes a legal activity
- Since the ethical hacker takes permission prior to hacking into a system, it is legally made sure that he has no malicious intent. This is normally performed by making the ethical hacker sign contracts that legally bind him to work towards the improvement of the security of the company
Ergo, an ethical hacker is a computer security specialist, who hacks into a system with the consent or permission of the owner to disclose vulnerabilities in the security of the system in order to improve it. Now, let us go over the roles of an ethical hacker in this ethical hacking tutorial.
Ready to lead the way in cybersecurity? Enroll in CISSP Training and get skilled.
Related Post : What Is a Honeypot in Cybersecurity?
Ethical Hacker Roles
Ethical hackers have various roles in the organization they work for. Considering the fact that ethical hacking is adopted by public and private organizations alike, goals may end up being diverse, but they can be boiled down to a few key points –

- Protect the privacy of the organization the ethical hacker is working for
 Immaculately report any sort of discrepancy in the system to the corresponding division with the responsibility of mending the vulnerability
Immaculately report any sort of discrepancy in the system to the corresponding division with the responsibility of mending the vulnerability Update hardware and software vendors regarding any sort of vulnerabilities found in their product, that is being used to orchestrate business
Update hardware and software vendors regarding any sort of vulnerabilities found in their product, that is being used to orchestrate business
Why is Ethical Hacking Important?
Data has become an invaluable resource. Accordingly, the preservation of privacy, and integrity of data has also increased in importance. In essence, this makes ethical hacking extremely important today! This is primarily due to the fact that almost every business out there has an internet facing side. Whether it be public relations, content marketing or sales, the internet is being used as a medium. This makes any endpoint that is being used to serve the medium, a possible vulnerability.
Furthermore, hackers of the present age, have proven themselves to be creative geniuses when it comes to penetrating into a system. Fighting fire with fire might not work in the real world, but to fight off a hacker so smart, an organization needs someone who has the same train of thought. Recent hacking outages have lead to losses amounting to millions of dollars. These incidents have cautioned businesses around the globe and made them rethink their stance on the importance of ethical hacking and cybersecurity.
Having laid down the grounds for ethical hackers after specifying their roles and importance to an organization, let us move forward and discuss some key elements of ethical hacking in this ethical hacking tutorial. If you want to start a career in Ethical Hacking, enroll in the Hacking Course training and get certified.
Upskill for Higher Salary with Cyber Security Courses
Course Name | Upcoming Batches | Fees |
| Cyber Security Certification Training | 20th April 2024 (Weekend Batch) | ₹14,995 |
| Certified Ethical Hacker Training | 18th April 2024 (Weekend Batch) | ₹42,000 |
| CISSP Certification Training | 27th April 2024 (Weekend Batch) | ₹19,995 |
What is a Security Threat?
As an ethical hacker, your daily routine will include dealing with a bunch of security threats.
Any risk that has the potential to harm a system or an organization as a whole is a security threat. Let’s go over the types of security threats.
Types of Security Threats
Threats are of two types:
Physical Threats
Physical threats are further divided into three categories.
- Internal e.g. hardware fire, faulty power supply, internal hardware failures etc
- External e.g. floods, fires, earthquakes etc
- Human e.g. vandalism, arson, accidental errors etc
Non-Physical Threats
Non-physical threats include every threat that has no physical manifestation. They are also known as logical threats. Below is a picture of the most common non-physical threats:

An ethical hacker generally deals with non-physical threats on a daily basis, and it is his responsibility, to come up with preventive measures for these threats.
Learn about the latest tools, technologies, and frameworks used in ethical hacking through this Ethical Hacking Internship.
Security Threats: Preventive Measures
While most preventive measures adopted by ethical hackers tend to differ for every organization due to customized needs, they can be boiled down to some key methodologies that are ubiquitously followed –
- Every organization must have a logical security measure in place. This could also include cognitive cybersecurity measures adopted by an organization which operates on an incident response system.
- Authentication can be improved and made more efficient by using multi-factor authentication systems. Authentication methods can be in the form of user IDs and strong passwords, smart cards, captchas, biometric, etc.
- For protection against entities like worms, trojans, viruses etc. organizations sometimes use specially curated anti-viruses that are made keeping the company’s special needs in mind. Additionally, an organization may also find it beneficial to use control measures on the use of external storage devices and visiting the website that is most likely to download unauthorized programs onto the target computer.
- Intrusion-detection/prevention systems can be used to protect against denial of service attacks. There are other measures too that can be put in place to avoid denial of service attacks.
Having discussed the types of threats an ethical hacker deals with regularly, let’s go over the skills that are required to be able to deal with the discussed threats in this ethical hacking tutorial.
Find out our Ethical Hacking Course in Top Cities
Ethical Hacker Skills

An ethical hacker is a computer expert, who specializes in networking and penetration testing. This generally entails the following skill set –
- Expertise in various operating systems, primarily Linux and its various distribution. This is because a good portion of vulnerability testing includes invading the target system and sifting through their system. This is impossible without a good grasp on operating systems.
- In-depth knowledge of networking is also key to a successful ethical hacking career. This involves packet tracking, packet sniffing, intrusion detection & prevention, scanning subnets etc.
- Programming: Now programming is a vast topic with nuances in every language. As an ethical hacker, it is not expected of you to be a master-coder, but rather be a jack-of-all-trades.
Below is a table of the major/commonly used programming languages. Knowing these will definitely help you as an ethical hacker:
| Language | Description | Reason to learn |
| HTML | Used for creating web pages | HTML forms are used to enter data all over the internet. Being able to construct your own forms for analyzing vulnerabilities helps to figure out security issues in the code |
| Javascript | Client-side scripting language. Also used for writing backend services | JavaScript code is executed on the client browser. Knowledge of JS can be used to read saved cookies and perform cross-site scripting etc. |
| SQL | Used for interacting with databases | Using SQL injection, to by-pass web application login algorithms that are weak, delete data from the database, etc. |
| PHP/Ruby | Server-side scripting. | PHP is one of the most used web programming languages. It is used to process HTML forms and performs other custom tasks. You could write a custom application in PHP that modifies settings on a web server and makes the server vulnerable to attacks. |
| Bash | Creating small batch files and handy scripts | They come in handy when you need to write your own shellcodes, exploits, rootkits or understanding and expanding on existing ones. |
Why Learn Programming?
Whenever I’ve mentioned that programming is an ethical hacking essential, I’ve been asked why. This is mostly because people do not have the slightest clue about the roles and responsibilities of an ethical hacker. Here are a few reasons that make programming knowledge crucial for an ethical hacking career:
- Ethical hackers are the problem solver and tool builders, learning how to program will help you implement solutions to problems.
- Programming also helps automate tasks that would generally take up precious time to complete
- Writing programs can also help you identify and exploit programming errors in applications that you will be targeting
- Programming knowledge also helps customize pre-existing tools to cater to your needs. For example, Metasploit is written in Ruby and you can add a new exploit to it if you know how to write one in Ruby
Talking about tools used in ethical hacking, let us go over a few of them.
Ethical Hacking Tools
It is impossible to go over every ethical hacking tool out there in a single article, hence, I’ll just be going over some of the really famous ones in this section:
Nmap
Nmap, short for Network Mapper, is a reconnaissance tool that is widely used by ethical hackers to gather information about a target system. This information is key to deciding the proceeding steps to attack the target system. Nmap is cross-platform and works on Mac, Linux, and Windows. It has gained immense popularity in the hacking community due to its ease of use and powerful searching & scanning abilities.
Netsparker
 Netsparker is a web application security testing tool. Netsparker finds and reports web application vulnerabilities such as SQL Injection and Cross-site Scripting (XSS) on all types of web applications, regardless of the platform and technology they are built with. Netsparker’s unique and dead accurate Proof-Based Scanning technology does not just report vulnerabilities, it also produces a Proof-of-Concept to confirm they are not false positives. Freeing you from having to double check the identified vulnerabilities.
Netsparker is a web application security testing tool. Netsparker finds and reports web application vulnerabilities such as SQL Injection and Cross-site Scripting (XSS) on all types of web applications, regardless of the platform and technology they are built with. Netsparker’s unique and dead accurate Proof-Based Scanning technology does not just report vulnerabilities, it also produces a Proof-of-Concept to confirm they are not false positives. Freeing you from having to double check the identified vulnerabilities.
Burpsuite
Burp Suite is a Java-based Web Penetration Testing framework. It has become an industry standard suite of tools used by information security professionals. Burp Suite helps you identify vulnerabilities and verify attack vectors that are affecting web applications. Burp Suit’s unquestionable acceptance and fame can be attributed to the fantastic web application crawler. It can –
- Accurately map content and functionality
- Automatically handling sessions
- Handles all sorts of state changes, volatile content, and application logins
Metasploit
Metasploit is an open-source pen-testing framework written in Ruby. It acts as a public resource for researching security vulnerabilities and developing code that allows a network administrator to break into his own network to identify security risks and document which vulnerabilities need to be addressed first. It is also one of the few tools used by beginner hackers to practice their skills. It also allows you to replicate websites for phishing and other social engineering purposes.
Talking about social engineering, let us take a moment to discuss the same.
What is Social Engineering?
Social engineering has proven itself to be a very effective mode of hacking amongst other malicious activities. The term encapsulates a broad range of malicious activities accomplished through human interactions. It uses psychological manipulation to trick users into committing security mistakes or giving away sensitive information.
Social engineering is a multi-step process. A perpetrator first investigates the intended victim to gather necessary background information, such as potential points of entry and weak security protocols, needed to proceed with the attack. Then, the attacker moves to gain the victim’s trust and provide stimuli for subsequent actions that break security practices, such as revealing sensitive information or granting access to critical resources.
The image below depicts the various phases of a social engineering attack:

Social Engineering Techniques
Moving forward in this ethical hacking tutorial, let us discuss the various methods used for social engineering.
 Familiarity Exploit
Familiarity Exploit
You always trust someone you are familiar with, don’t you? That’s exactly what social engineering evangelists take advantage of! The perpetrator might get themselves familiarised with the chosen target with day to day methodologies which have a facade of friendliness painted all over it. These can include activities like joining someone for a smoke, going out for drinks, playing video games etc.
 Phishing
Phishing
Phishing has proven itself to be a fantastic approach to social engineering. Phishing involves creating counterfeit websites that have the look and feel of a legitimate website. People who visit the website are tricked into entering their credentials that are then stored and redirected to the hacker’s system.
Exploiting Human Emotions
 Exploiting human emotions is probably the easiest craft of social engineering. Feelings like greed and pity are very easily triggered. A social engineer may deliberately drop a virus infected flash disk in an area where the users can easily pick it up. The user will most likely plug the flash disk into the computer. The drive may be infested with all sorts of nonphysical threats which may actually be an infected file.
Exploiting human emotions is probably the easiest craft of social engineering. Feelings like greed and pity are very easily triggered. A social engineer may deliberately drop a virus infected flash disk in an area where the users can easily pick it up. The user will most likely plug the flash disk into the computer. The drive may be infested with all sorts of nonphysical threats which may actually be an infected file.
It is an ethical hacker’s job to spread awareness about such techniques in the organization he/ she works for. Now let’s take a moment to talk about cryptography and cryptanalysis in this ethical hacking tutorial.
Cryptography
Cryptography is the art of ciphering text into an unreadable format. Just in case your data falls into the wrong hand, you can stay at ease as long as it is well encrypted. Only the person with the decryption key will be able to see the data. An ethical hacker is more interested in the working of algorithms that let him decipher the data without the key. This is called cryptanalysis.
 Cryptanalysis
Cryptanalysis
Cryptanalysis is the study of analyzing information systems in order to study the hidden aspects of the systems. Cryptanalysis is used to breach cryptographic security systems and gain access to the contents of encrypted messages, even if the cryptographic key is unknown. Methodologies like Brute force, Dictionary attacks, Rainbow table attacks have all stemmed from cryptanalysis. The success of cryptanalysis depends on the time one has, the computing power available and also the storage.
Standard Cryptographic Algorithms
Let’s discuss some of the most common cryptographic algorithms used till date:
MD5– this is the acronym for Message-Digest 5. It is used to create 128-bit hash values. Theoretically, hashes cannot be reversed into the original plain text. MD5 is used to encrypt passwords as well as check data integrity. MD5 is not collision resistant. Collision resistance is the difficulties in finding two values that produce the same hash values.
SHA– this is the acronym for Secure Hash Algorithm. SHA algorithms are used to generate condensed representations of a message (message digest). It has various versions such as;
- SHA-0: produces 120-bit hash values. It was withdrawn from use due to significant flaws and replaced by SHA-1.
- SHA-1: produces 160-bit hash values. It is similar to earlier versions of MD5. It has cryptographic weakness and is not recommended for use since the year 2010.
- SHA-2: it has two hash functions namely SHA-256 and SHA-512. SHA-256 uses 32-bit words while SHA-512 uses 64-bit words.
- SHA-3: this algorithm was formally known as Keccak.
RC4 – this algorithm is used to create stream ciphers. It is mostly used in protocols such as Secure Socket Layer (SSL) to encrypt internet communication and Wired Equivalent Privacy (WEP) to secure wireless networks.
Hacktivity – RC4 Decryption Demonstration
In this practical application of decryption, we are going to try and decrypt an RC4 encrypted text using a tool called Cryptool. We are going to encrypt a piece of text using RC4 and then try to decrypt it.
Step 1: After installing Cryptool, launch it on your system. An identical window should pop-up.
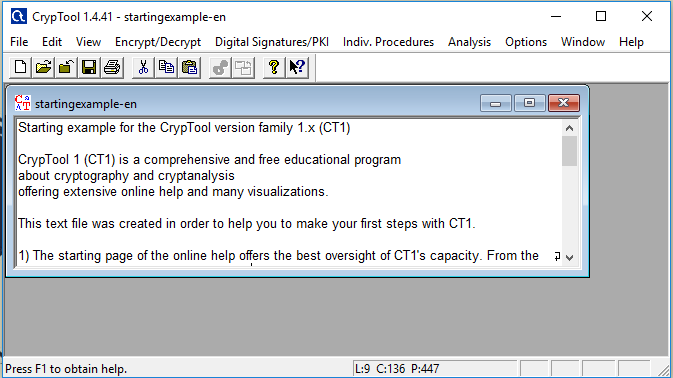
Step 2: Replace the text you see in the window with whatever you want. For this particular example, I’ll be using the phrase:

Step 3: Choose the RC4 encryption algorithm to encrypt your text.

Step 4: Set the key length to 24 bits and the value to ’00 00 00′.

Step 5: Encrypt!

You should get an output like this. This is the ciphertext of the plain text you entered.

Step 6: On the analysis tab choose RC4.
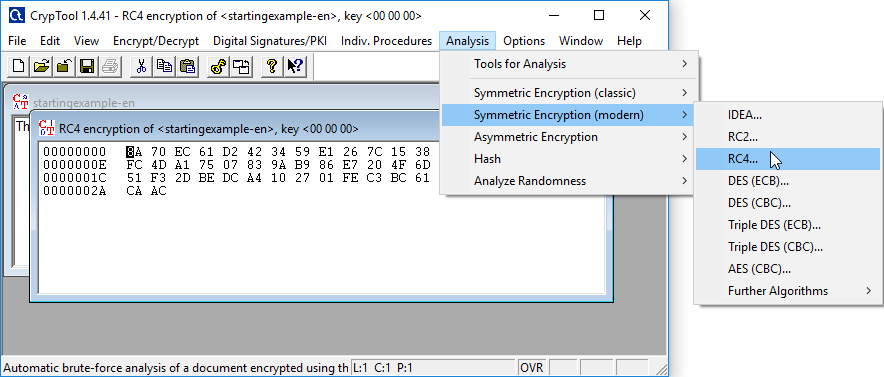
Step 7: Set the key length to 24 bits.

Step 8: Wait for it Decrypt!
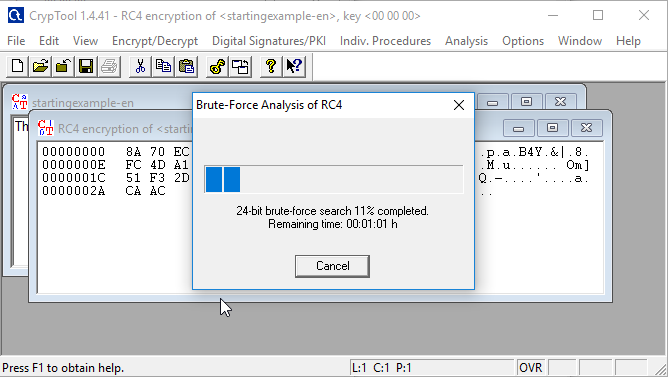
Step 9: The value with the lowest entropy should be the original plain text.

This brings us to the end of this ethical hacking tutorial. For more information regarding cybersecurity, you can check out my other blogs. If you wish to learn Cybersecurity and build a colorful career in this domain, then check out our Cyber Security Certification Training which comes with instructor-led live training and real-life project experience. This training will help you understand cybersecurity in depth and help you achieve mastery over the subject.
You can also take a look at our newly launched course on CompTIA Security+ Certification Course which is a first-of-a-kind official partnership between Edureka & CompTIA Security+. It offers you a chance to earn a global certification that focuses on core cybersecurity skills which are indispensable for security and network administrators.
Learn Cybersecurity the right way with Edureka’s cyber security masters program and defend the world’s biggest companies from phishers, hackers and cyber attacks.































![Online Cyber Security Course with Certificate [2024]](https://d1jnx9ba8s6j9r.cloudfront.net/imgver.2408291244/img/co_img_1269_1695895774.png)





