Cyber Security and Ethical Hacking Internship ...
- 15k Enrolled Learners
- Weekend/Weekday
- Live Class
Cybercrime is a global problem that’s been dominating the news cycle. It poses a threat to individual security and an even bigger threat to large international companies, banks, and governments. Today’s organized cybercrimes far out shadow lone hackers of the past now large organized crime rings function like start-ups and often employ highly-trained developers who are constantly innovating online attacks. With so much data to exploit out there, Cybersecurity has become essential. Hence, I decided to write up this blog on “What is Cybersecurity?”
This Edureka Cyber Security Tutorial will help you learn in-depth Cyber Security Concepts.
Before we begin, let me just list out the topics I’ll be covering through the course of this blog.

The golden age of Hackers – What is Cyber security – Edureka
It can be rightfully said that today’s generation lives on the internet, and we general users are almost ignorant as to how those random bits of 1’s and 0’s reach securely to our computer. For a hacker, it’s a golden age. With so many access points, public IP’s and constant traffic and tons of data to exploit, black hat hackers, are having one hell of a time exploiting vulnerabilities and creating malicious software for the same. Above that, cyber-attacks are evolving by the day. Hackers are becoming smarter and more creative with their malware and how they bypass virus scans and firewalls still baffles many people.
Therefore there has to be some sort of protocol that protects us against all these cyberattacks and makes sure our data doesn’t fall into the wrong hands. This is exactly why we need cybersecurity and to learn about it you must go for Cyber Security Masters program.
Let’s see some of the most common cyber attacks that have plagued us as a community since the beginning of the internet.
Go through our CEH (v12)- Certified Ethical Hacker program to explore more about ethical hacking which will teach you the most current hacking techniques, cyber security tools and methods that hackers use.
Join the elite cybersecurity professionals and boost your career with CISSP Certification.
Types of Cyberthreats – What is meant by Cyber security – Edureka
From a computing point of view, security comprises cybersecurity and physical security — both are used by enterprises to protect against unauthorized access to data centers and other computerized systems. Information security, which is designed to maintain the confidentiality, integrity, and availability of data, is a subset of cybersecurity. The use of cyber security can help prevent cyber attacks, data breaches, and identity theft and can aid in risk management.
So when talking about cybersecurity, one might wonder “What are we trying to protect ourselves against?” Well, there are three main aspects we are trying to control, name:
These three terms are synonymous with the very commonly known CIA triad which stands for Confidentiality, Integrity, and Availability. The CIA triad is also commonly referred to as the three pillars of security and most of the security policies of an organization are built on these three principles.
Enroll in a prestigious Cyber Security Internship program to kickstart your career.
Find out our Cyber Security Training in Top Cities/Countries
| India | USA | Other Cities/Countries |
| Bangalore | New York | UK |
| Hyderabad | Chicago | London |
| Delhi | Atlanta | Canada |
| Chennai | Houston | Toronto |
| Mumbai | Los Angeles | Australia |
| Pune | Boston | UAE |
| Kolkata | Miami | Dubai |
| Ahmedabad | San Francisco | Philippines |
The CIA triad which stands for Confidentiality, Integrity, and Availability is a design model to guide companies and organizations to form their security policies. It is also known as the AIC triad to avoid confusion with Central Intelligence Agency(CIA). The components of the triad are considered to be the most important and fundamental components of security. So let me brief you all about the three components
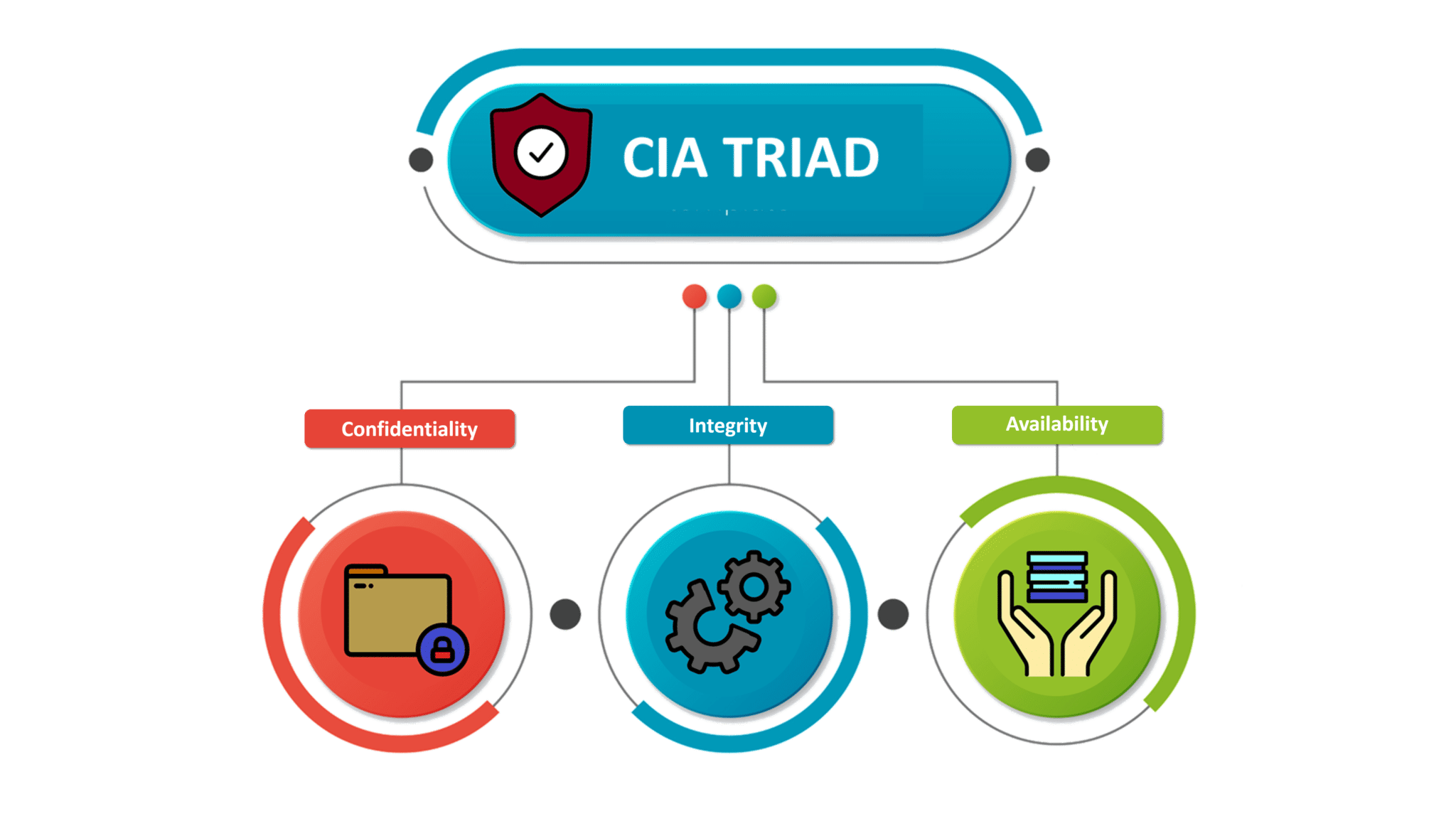
CIA Triad – What is Cyber security – Edureka
Confidentiality is the protection of personal information. Confidentiality means keeping a client’s information between you and the client, and not telling others including co-workers, friends, family, etc.
Integrity, in the context of computer systems, refers to methods of ensuring that data is real, accurate and safeguarded from unauthorized user modification.
Availability, in the context of a computer system, refers to the ability of a user to access information or resources in a specified location and in the correct format.
Attacks on CIA – What is Cyber security – Edureka
Find out our Cyber Security Course in Top Cities
There are numerous procedures for actually implementing cybersecurity, but there three main steps when actually fixing a security-related issue.
The first step is to recognize the problem that is causing the security issue, for example, we have to recognize whether there is a denial of service attack or a man in the middle attack. The next step is to evaluate and analyze the problem. We have to make sure we isolate all the data and information that may have been compromised in the attack. Finally, after evaluating and analyzing the problem, the last step is to develop a patch that actually solves the problem and brings back the organization to a running state.
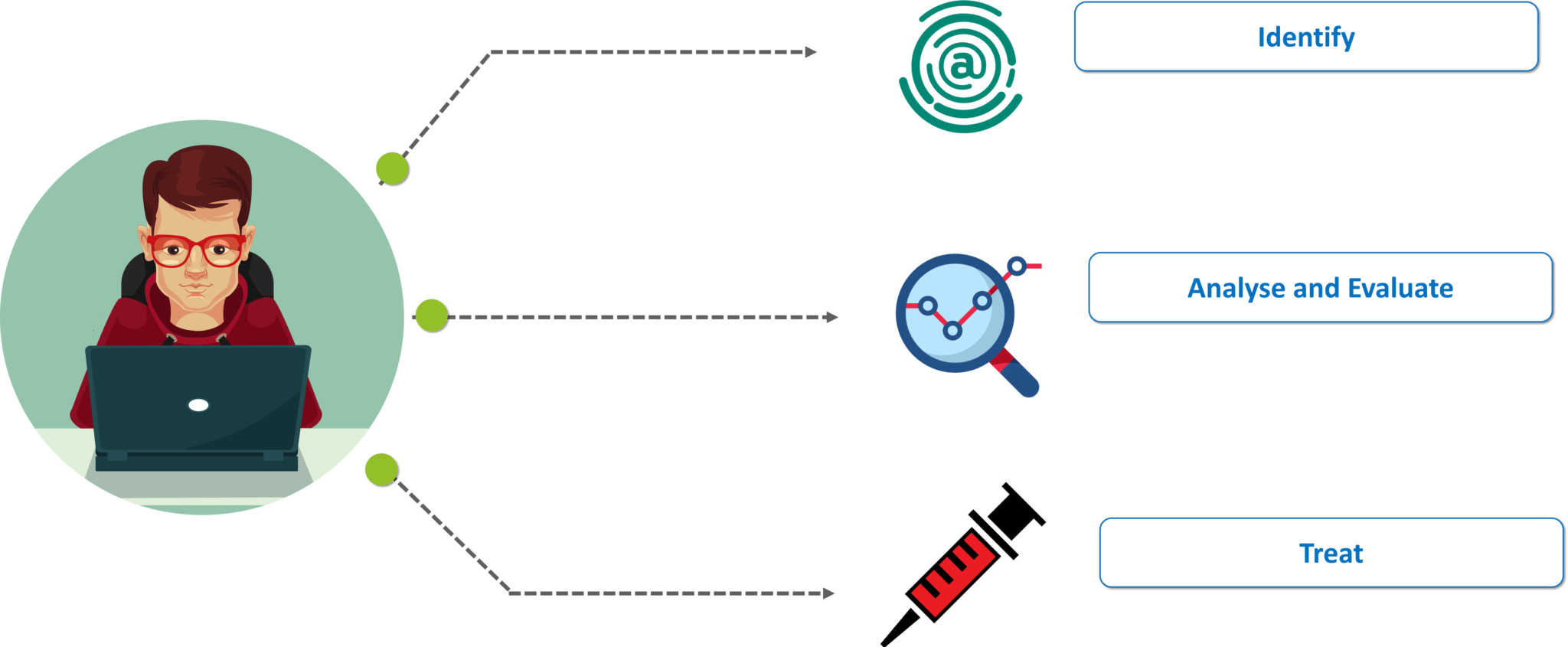
Steps to treat a Cyberattack – What is Cybersecurity – Edureka
When identifying, analyzing and treating a cyber attack, there are three principals that are kept in mind for various calculations. They are:
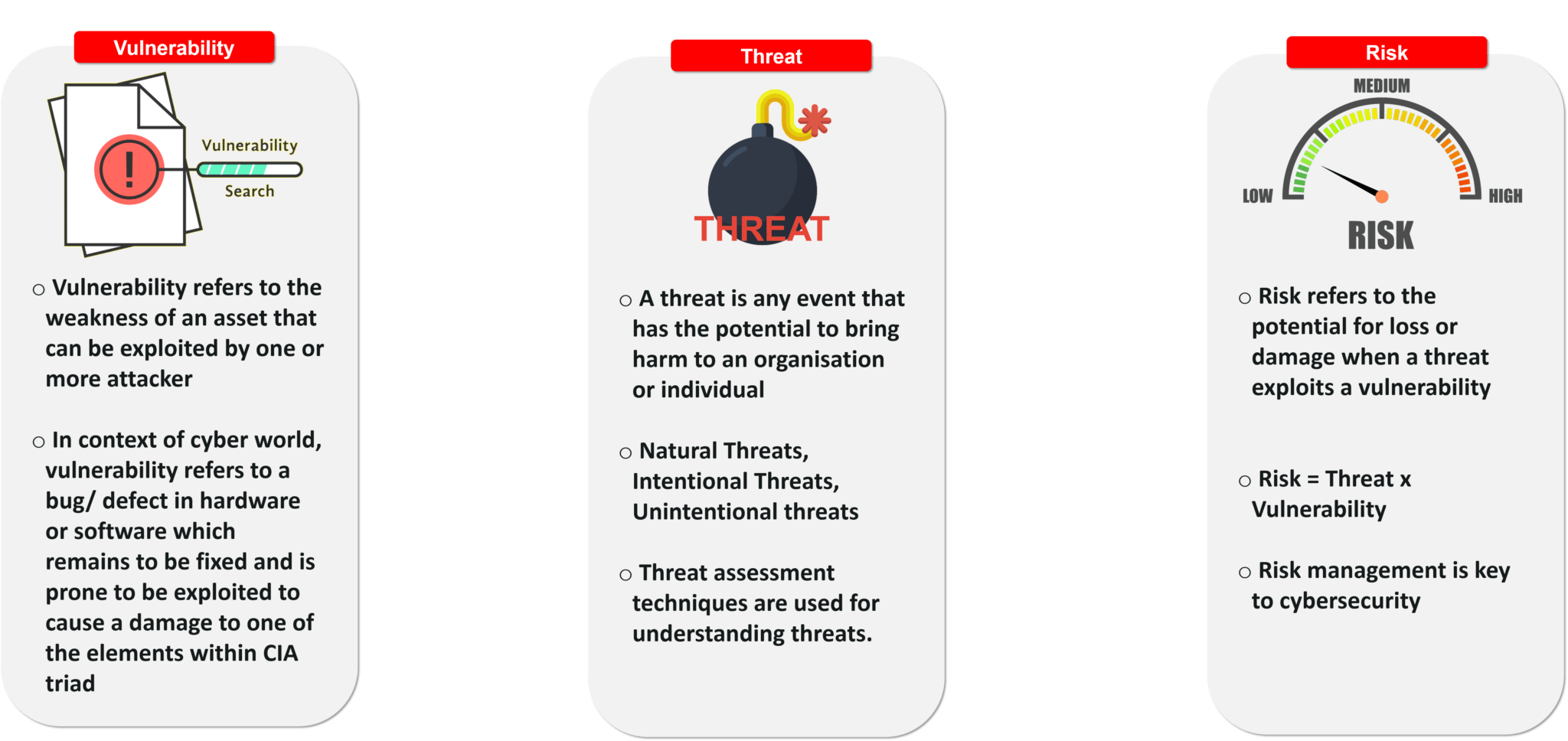
Vulnerability, Threat and Risk – What is Cybersecurity – Edureka
Course Name | Upcoming Batches | Fees |
| Cyber Security Certification Training | 20th April 2024 (Weekend Batch) | ₹14,995 |
| Certified Ethical Hacker Training | 18th April 2024 (Weekend Batch) | ₹42,000 |
| CISSP Certification Training | 27th April 2024 (Weekend Batch) | ₹19,995 |
If you wish to learn cybersecurity and build a colorful career in cybersecurity, then check out our Cyber Security Certification Course Training which comes with instructor-led live training and real-life project experience. This training will help you understand cybersecurity in-depth and help you achieve mastery over the subject. You can also take a look at our newly launched CompTIA Security+ Certification Course which is a first-of-a-kind official partnership between Edureka & CompTIA Security+. It offers you a chance to earn a global certification that focuses on core cybersecurity skills which are indispensable for security and network administrators.
Got a question for us? Please mention it in the comments section and we will get back to you or join our Cyber Security Training in Malang today.
| Course Name | Date | Details |
|---|---|---|
| Online Cyber Security Course with Certificate [2024] | Class Starts on 31st August,2024 31st August SAT&SUN (Weekend Batch) | View Details |
| Online Cyber Security Course with Certificate [2024] | Class Starts on 28th September,2024 28th September SAT&SUN (Weekend Batch) | View Details |
 REGISTER FOR FREE WEBINAR
REGISTER FOR FREE WEBINAR  Thank you for registering Join Edureka Meetup community for 100+ Free Webinars each month JOIN MEETUP GROUP
Thank you for registering Join Edureka Meetup community for 100+ Free Webinars each month JOIN MEETUP GROUP
edureka.co

Thanks for sharing this content with us, your content is really helpful for me, you describe it very well and keep posting.
thanks
Very simplified.
Thanks