Cyber Security and Ethical Hacking Internship ...
- 15k Enrolled Learners
- Weekend/Weekday
- Live Class
You can find the essence of technology everywhere. As businesses increase their dependency on Information Technology including Cloud, IoT, mobile devices, and social media, their cyber risk continues to rise at an alarming rate. Almost every day, you can find a new headline regarding the latest cybersecurity attack. Hackers are improving their methods and are still stealing millions of records and billions of dollars at an alarming frequency. One way to combat these attacks is through Penetration Testing. In this article, we will explore what is Penetration Testing and its types. It will answer all the following questions regarding Penetration Testing:
Let’s get started!
Penetration Testing is answering a simple question: “What would a cybercriminal do to harm my organization’ computer systems, applications, and network?“. It is the practice of testing a computer system, network or web application to find vulnerabilities that an attacker could exploit, simulating an attack against an organization’s IT assets.
Vulnerabilities could be due to multiple reasons, few basic ones being:
So, an efficient penetration testing helps in finding the gaps in the security tools that an organization is using, finds multiple attack vectors and misconfigurations. So an organization can prioritize the risk, fix it and improve the overall security response time. Moving forward, with this ‘What is Penetration Testing?’ article we will learn how a typical penetration test is carried out.
Penetration Testing Tutorial | Penetration Testing using Metasploit | Edureka
This Edureka Tutorial video on “Penetration Testing Tutorial” gives an introduction to Web Application penetration testing using metasploit and metasploitable2.
Penetration tester usually begins by gathering as much information about the target as possible. Then he identifies the possible vulnerabilities in the system by scanning. After which he launches an attack. Post-attack he analyses each vulnerability and the risk involved. Finally, a detailed report is submitted to higher authorities summarizing the results of the penetration test.
Penetration testing can be broken down into multiple phases, this will vary depending on the organization and the type of penetration test.
Let’s discuss each phase:
The first phase is planning. Here, the attacker gathers as much information about the target as possible. The data can be IP addresses, domain details, mail servers, network topology, etc. In this phase, he also defines the scope and goals of a test, including the systems to be addressed and the testing methods to be used. An expert penetration tester will spend most of the time in this phase, this will help with further phases of the attack.
Based on the data collected in the first step, the attacker will interact with the target with an aim to identify the vulnerabilities. This helps a penetration tester to launch attacks using vulnerabilities in the system. This phase includes the use of tools such as port scanners, ping tools, vulnerability scanners, and network mappers.
While testing web applications, the scanning part can be either dynamic or static.
Ready to lead the way in cybersecurity? Enroll in CISSP Training and get skilled.
This is the crucial phase that has to be performed with due care. This is the step where the actual damage is done. Penetration Tester need to have some special skills and techniques to launch an attack on the target system. Using these techniques an attacker will try to get the data, compromise the system, launch dos attacks, etc. to check to what extent the computer system or application or a network can be compromised.
After the penetration test is complete, the final goal is to collect the evidence of the exploited vulnerabilities. This step mostly considers all the steps discussed above and an evaluation of the vulnerabilities present in the form of potential risks. Sometimes, in this step pen-tester also provides some useful recommendations to implement in order to improve security levels.
Now, this is the final and the most important step. In this step, the results of the penetration test are compiled into a detailed report. This report usually has the following details:
These phases may sometimes vary depending on the organization and the type of penetration test being conducted. This ‘What is Penetration Testing?’ article further explores different Penetration Testing types.
Check out our new CEH Course to learn the in-depth concepts of ethical hacking and get skilled.
Find out our Cyber Security Course in Top Cities
Penetration testing can be categorized based on different parameters like the knowledge of the target or the position of the penetration tester or the areas where it is performed.
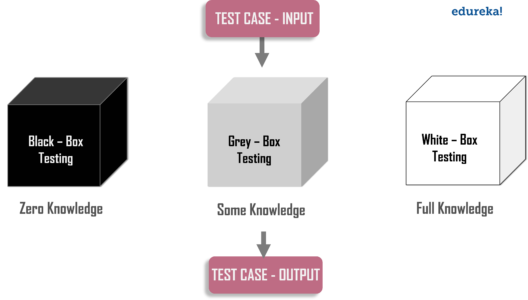
Black Box
When the attacker has no knowledge of the target, it is referred to as a black box penetration test. This type requires a lot of time and the pen tester uses automated tools in order to find vulnerabilities and weak spots.
White Box
When the penetration tester is given the complete knowledge of the target, it is called as white box penetration test. The attacker has complete knowledge of the IP addresses, controls in place, code samples, operating system details etc. It requires less time when compared to black box penetration testing.
Grey Box
When the tester is having partial information about the target, it is referred to as gray box penetration testing. In this case, the attacker will have some knowledge of the target information like URLs, IP addresses, etc., butwill not have complete knowledge or access.
Explore various domains of Cybersecurity through this Cyber Security Internship, including Network Security, Cryptography and Web Application Hacking.
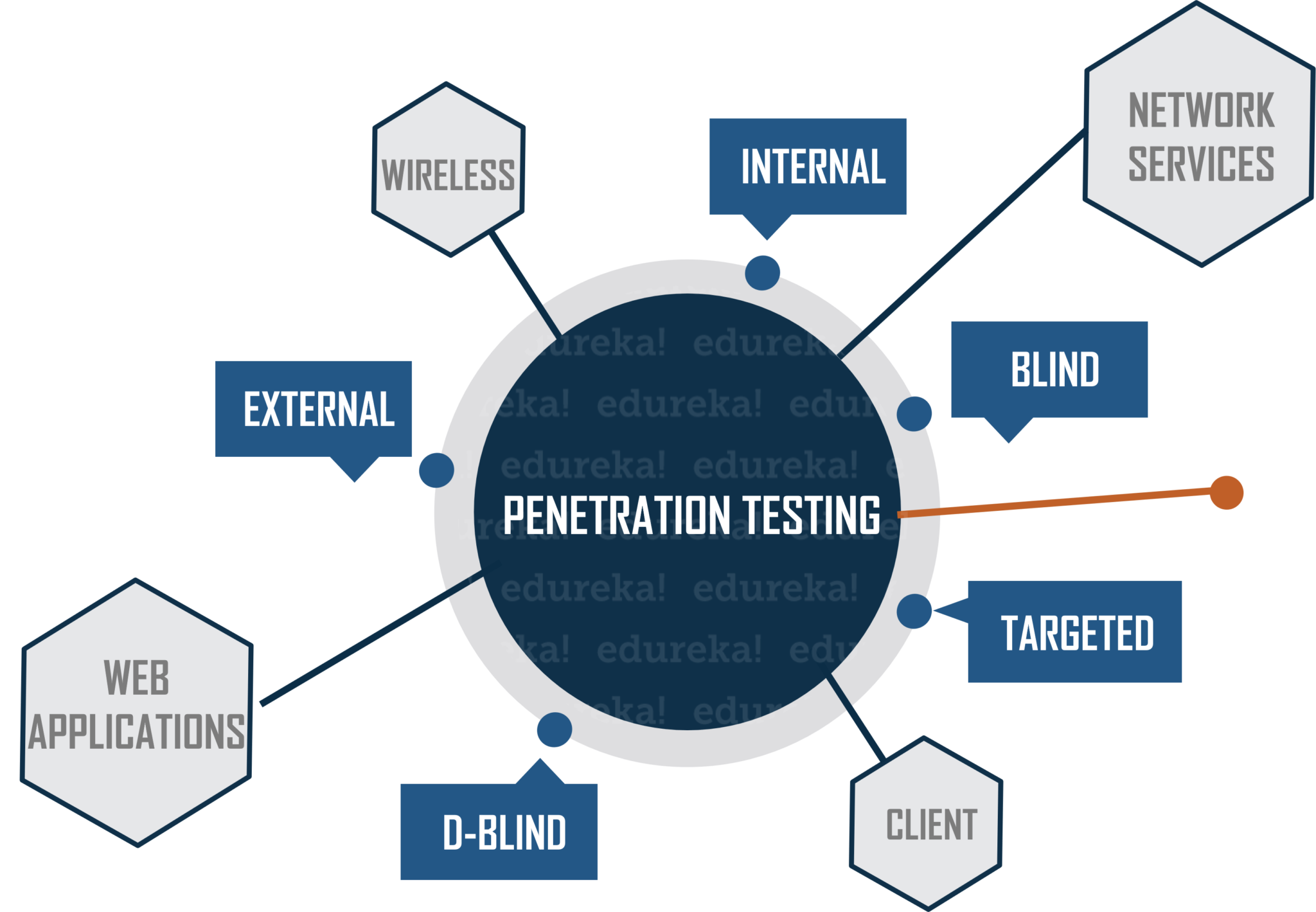
Network Penetration Testing
Network Penetration Testing activity aims at discovering weaknesses and vulnerabilities related to the network infrastructure of the organization. It involves, firewall configuration & bypass testing, Stateful analysis testing, DNS attacks etc. Most common software packages which are examined during this test include:
Application Penetration Testing
In Application Penetration Testing, penetration tester checks, if any security vulnerabilities or weaknesses are discovered in web-based applications. Core application components such as ActiveX, Silverlight, and Java Applets, and APIs are all examined. Therefore this kind of testing requires a lot of time.
Wireless Penetration Testing
In Wireless Penetration Testing, all of the wireless devices which are used in a corporation are tested. It includes items such as tablets, notebooks, smartphones, etc. This test spots vulnerabilities in terms of wireless access points, admin credentials, and wireless protocols.
Social Engineering
Social Engineering Test involves attempting to get confidential or sensitive information by purposely tricking an employee of the organization. You have two subsets here.
Client Side Penetration Testing
The purpose of this type of testing is to identify security issues in terms of software running on the customer’s workstations. It primary goal is to search and exploit vulnerabilities in client-side software programs. For example, web browsers (such as Internet Explorer, Google Chrome, Mozilla Firefox, Safari), content creation software packages (such as Adobe Framemaker and Adobe RoboHelp), media players, etc.
So, these are different types of penetration test based on different parameters. Now, in the remaining of this ‘What is Penetration Testing?’ article we will talk about the tools that a penetration tester can use to conduct a penetration test.
Penetration testers take the aid of different kinds of penetration tools to make the penetration test much faster, efficient, easy, and reliable. There are a lot of popular Penetration Testing tools, where most of them are free or open source software. Some of the most widely used pen testing tools include:
Apart from the above ones, there are others like John the Ripper, Burp Suite, Cain and Abel, and many more popular tools.
Well, we have reached the end of this article. So, know you know what is Penetration Testing, its phases, types, and tools. So, if you are curious as to how to perform penetration testing using Metasploit Framework, you can refer to the Penetration Testing Tutorial video below.
Penetration Testing Tutorial | Cyber Security Training | Edureka
This Edureka video on “Penetration Testing” will help you understand all about penetration testing, its methodologies, and tools.
If you wish to learn cybersecurity and build a colorful career in cybersecurity, then check out our Cyber Security Course Online which comes with instructor-led live training and real-life project experience. This training will help you understand cybersecurity in depth and help you achieve mastery over the subject.
You can also take a look at our newly launched CompTIA Security+ Certification course which is a first-of-a-kind official partnership between Edureka & CompTIA Security+. It offers you a chance to earn a global certification that focuses on core cybersecurity skills which are indispensable for security and network administrators.
Learn Cybersecurity the right way with Edureka’s Cyber Security Masters program and defend the world’s biggest companies from phishers, hackers and cyber attacks.
Got a question for us? Please mention it in the comments section of “What is Penetration Testing?” and we will get back to you.
| Course Name | Date | Details |
|---|---|---|
| Online Cyber Security Course with Certificate [2024] | Class Starts on 31st August,2024 31st August SAT&SUN (Weekend Batch) | View Details |
| Online Cyber Security Course with Certificate [2024] | Class Starts on 28th September,2024 28th September SAT&SUN (Weekend Batch) | View Details |
 REGISTER FOR FREE WEBINAR
REGISTER FOR FREE WEBINAR  Thank you for registering Join Edureka Meetup community for 100+ Free Webinars each month JOIN MEETUP GROUP
Thank you for registering Join Edureka Meetup community for 100+ Free Webinars each month JOIN MEETUP GROUP
edureka.co
